A few days ago, I repaired a malware-infected WordPress site. WordPress itself is secure but the level of security could be compromised when you do not update the WordPress core files, themes or plugins in a timely way.
After deleting malicious code from database, I checked the web server and removed some strange files. I could not find additional suspected files.
I installed the Wordfence Security plugin and scanned the site for malware.
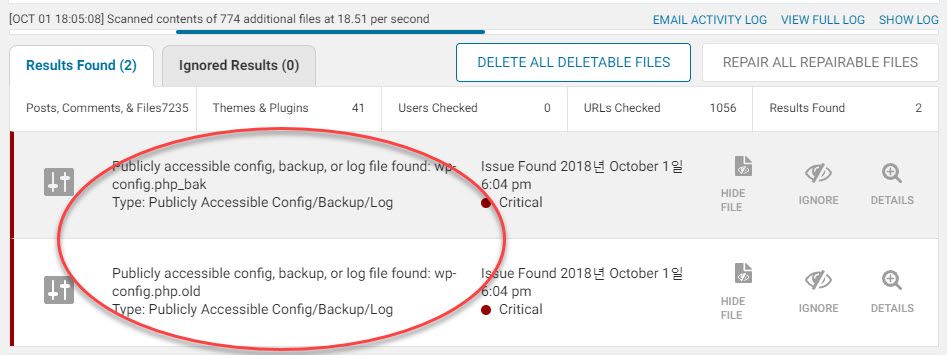
Two critical warnings were displayed when the scan completed. There was a backup file of config.php. I think someone updated the config.php file and left the old file as a backup. However, it might be publicly accessible and insecure and all such files need to be removed. (It'll be better to store them in your desktop or cloud server.)
You know, Duplicator is a handy tool for migrating WordPress installations from one server to another. However, some users leave the Duplicator backup files (including a script file) in the server, which also could be very dangerous.
It's strongly recommended to delete any Duplicator backup files from the server after restoring your site.
Since WordPress is very popular, vicious hackers target WordPress sites which have not been patched in a timely manner. Therefore, always maintain your WP site safely by updating the WordPress core files, themes and plugins to their latest version.